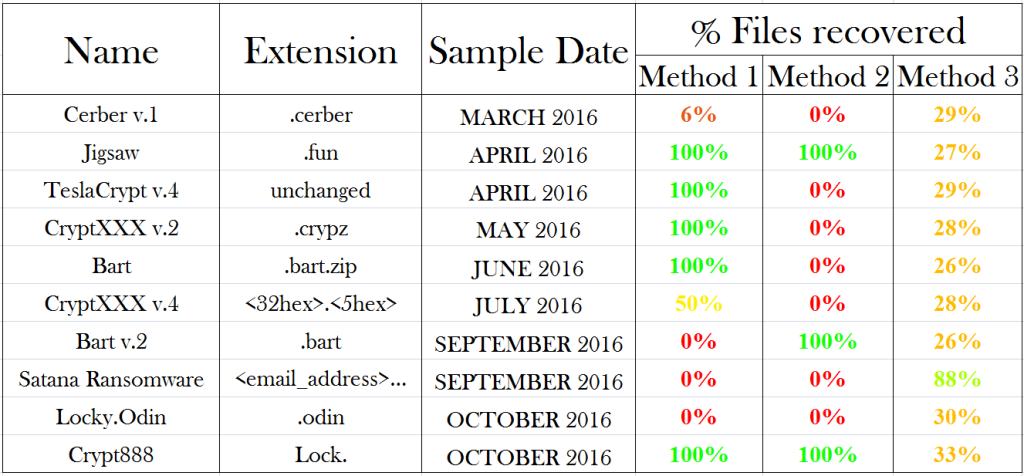
This post if about the power of big tech companies like Microsoft (I have had similar experiences with Google), and also about the human touch being replaced by AI. About artificial intelligence make decisions, and the failure to provide effective channels to correct mistakes made by AI.
I normally never beg for up-votes, shares or likes. However if you want to help small developers, please share this post! Make AV companies aware that flaws in their software are not without consequences. That leaving decisions to AI without human backup is not the way forward!
I like to see myself as an honest person, making honest software. I am not a brilliant programmer but I give it my best. I try to learn as much as I can about the problem it tries to tackle or to help you tackle. I once made the mistake of letting one of my tools to ping my web server so I could see how often the tool was run. People didn’t like this, wondered why it needed to connect to the internet. And so I removed it. The software tries to do what it is supposed to do. Scan a drive. Load a JPEG. Nothing more and nothing less. Maybe not the best software in the world, but honest software.
Submit a false positive and get a free license.
What I need you to do: Download JPEG-Repair. You may need to tell Defender or other AV software to ignore the ZIP. Disabling Cloud protection for a second may work too.
Instructions for Defender: Goto https://www.microsoft.com/en-us/wdsi/filesubmission. A Microsoft account is not required. Submit as home customer. Upload the ZIP file you downloaded from this website. Select ‘Incorrectly detected as malware/malicious’. Confirm submission (you may need to fill out Captcha).
At the bottom of the page there are more URL’s to AV vendors to which you can report a false positive.
Make a screenshot clearly showing the submission ID. Email me that screenshot and get a free license. The license is for personal use only and can not be shared with others.
If you are using a different AV product, email me the screenshot of the detection and the finished false positive submission form to get a free license. The license is for personal use only and can not be shared with others.
So, in short: Provide me with evidence of the detection and of you having submitted the file to the AV vendor of the software that detected it.
These are instructions for Windows Defender. To run JpegDigger.exe and JPGRepair.exe despite the (false) warning:
- Open Windows Defender Security Center.
- Click Virus & threat protection.
- Click the Virus & threat protection option.
- Under “Exclusions,” click the Add or remove exclusions option.
- Click the Add an exclusion button.
Windows Defender false positive
Unfortunately, sometimes my tools are falsely detected as malware by major anti virus and security software. Without exception they’re ‘flagged’ by the heuristic or AI portion of the AV software. This heuristic or AI (artificial intelligence) is supposed to learn to recognize malware so it can detect threats it has never seen before. Artificial intelligence may sound sophisticated, but it’s basically trying to come up with rules of thumb to distinguish innocent software versus malware.
Simple rules of thumb could be ‘is the software relatively unknown’ (my software is, but specially after I just released an update), or are certain strings present in the software like encrypt, bitcoin, hash, decrypt – my software does several hash and encryption routines when handling the registration key. JpegDigger also tries to figure out if a drive it’s scanning possibly contains encrypted data. Is the software accessing the internet, what is it trying to access on the internet (again, simply scan for URL’s), those type of things. Or, is the software trying to mask it’s accessing the internet? JpegDigger and JPEG-Repair do not access the internet unless you click a help link (like more info). I try to make it obvious these are URL’s by mimicking URL’s in web browsers, in blue and under-lined.
I can see how this can work, I can also see how these rule sets can cause innocent software to to flagged as malware. This is bound to happen and it can not be avoided. I accept this as a fact of life.
But then, when I become aware of my software being flagged because I notice this when scanning it in VirusTotal or a user notifies me, then I should be allowed to appeal this in a straight forward fashion (false positive submission). And I also expect AV software vendors to treat such requests with some sense of urgency. As I write this I am waiting for 3 days already for Microsoft to process a false positive report!! I find this unacceptable to be honest. If you decide to relay the decision on whether something is malware or not to AI (Microsoft claims this), then you need human backup to quickly correct mistakes made by the AI.
It will not come as a surprise that processing of false positives can be expedited by paying Microsoft for it.
Microsoft touts about it’s cloud delivered AI to protect your PC. Practice shows this AI can be flawed and there’s no effective backup mechanism to appeal AI decisions in place.
Stop whining, just file a false positive report
Now you may think, Joep stop your whining, there are bigger problems to worry about. But for me, this is quite an issue. This is kind of the equivalent of a security guard standing in front of my store and denying potential customers because he ‘thinks’ they look like they may have malintent. And you as a potential customer are sent away and denied access to my store against your will. So you see how this affect both you and me.
Frustration levels rise when the portal you can use to submit false positives appears flawed itself. You can tick whether you’re reporting a suspected virus – or – a suspected false positive. I of course pick the false positive option because I know my tools aren’t malware. The summary page however consistently shows ‘user opinion: malware’, which is NOT what I selected.
Why does this hit small developers
I do not mean short people. I mean developers that aren’t backed up by loads of cash an fancy lawyers.
This false flagging is a fact of life for virtually all small developers: The files they produce are relatively unknown, specially after just having updated them. The domain from which they distribute the files is relatively unknown. The cost of a digital code signing certificate may not outweigh the gain. They may program in a more obscure or older programming language. This language may be popular among writers of viruses and Trojans and whatnot.
So then what happens next .. Say you want to download my tools and Windows Defender or whatever they call it these days pops up with a warning. It tells you the software is dangerous and it quarantines it. You’re one of those kind people that sends me an email to make me aware if this. I assure you the software is not and does not contain malware and you believe me. I then explain you how you can tell Defender to ignore my program. And of course you discover nothing bad happens. My tools do not keep your data hostage, does not phone home, none of that. So now you know your anti virus program can be wrong.
Maybe you decide to disable ‘cloud intelligence’ all together, because that’s where Defender’s most false positives originate.
A virus slipping through (false negative) just as well as a innocent program being blocked (false positive) both illustrate the touted Cloud delivered AI is not perfect. Any of those happening should be reason for Microsoft to swiftly correct errors to maintain and restore trust in the product.
I have had similar issues with Google. An utterly frustrating experience due to lack of ways to contact any human being within those large tech companies that can actually help you. Seems a law of the universe, Large Tech is actually evil.
http://straighttips.blogspot.com/2019/12/virustotal-report-false-positives.html
https://blog.nirsoft.net/2009/05/17/antivirus-companies-cause-a-big-headache-to-small-developers/
https://weblog.west-wind.com/posts/2016/oct/05/dealing-with-antivirus-false-positives
https://stackoverflow.com/questions/40960407/my-c-sharp-program-is-detected-as-a-virus
Reporting a false-positive
I recommend reporting a false-positive directly to your anti-virus vendor.
Here is a list of some vendors and their instructions for reporting false-positives:
- Avast
- AVG
- Bitdefender
- ESET
- Kaspersky
- McAfee
- Norton Antivirus
- SonicWall
- Symantec
- Trend Micro
- Webroot
- Windows Defender
The post AV False positives are a plague, specially those by AI appeared first on JPEG Repair | Photo Recovery | File Recovery | Video Recovery.





















 .
.